Block Chain Addition and Security
Blockchain Chains Are Added and Secured
How Blockchain Chains Are Added and Secured

Introduction
The security and integrity of blockchain technology lies in its sophisticated process of adding new blocks and protecting the entire chain. Understanding these mechanisms reveals why blockchain is considered one of the most secure data storage systems ever created. This blog explores the step-by-step process of how blockchain chains grow and remain tamper-proof.
The Blockchain Structure
Understanding blockchain structure is fundamental to grasping how security is maintained. Every blockchain consists of blocks that contain both data and metadata, organized in a specific format that enables verification and linkage.
Block Anatomy
The block header is the control center of each block, containing critical information that enables the blockchain's security and functionality. Think of it as a summary card that tells the network everything it needs to know about the block without examining every transaction inside.
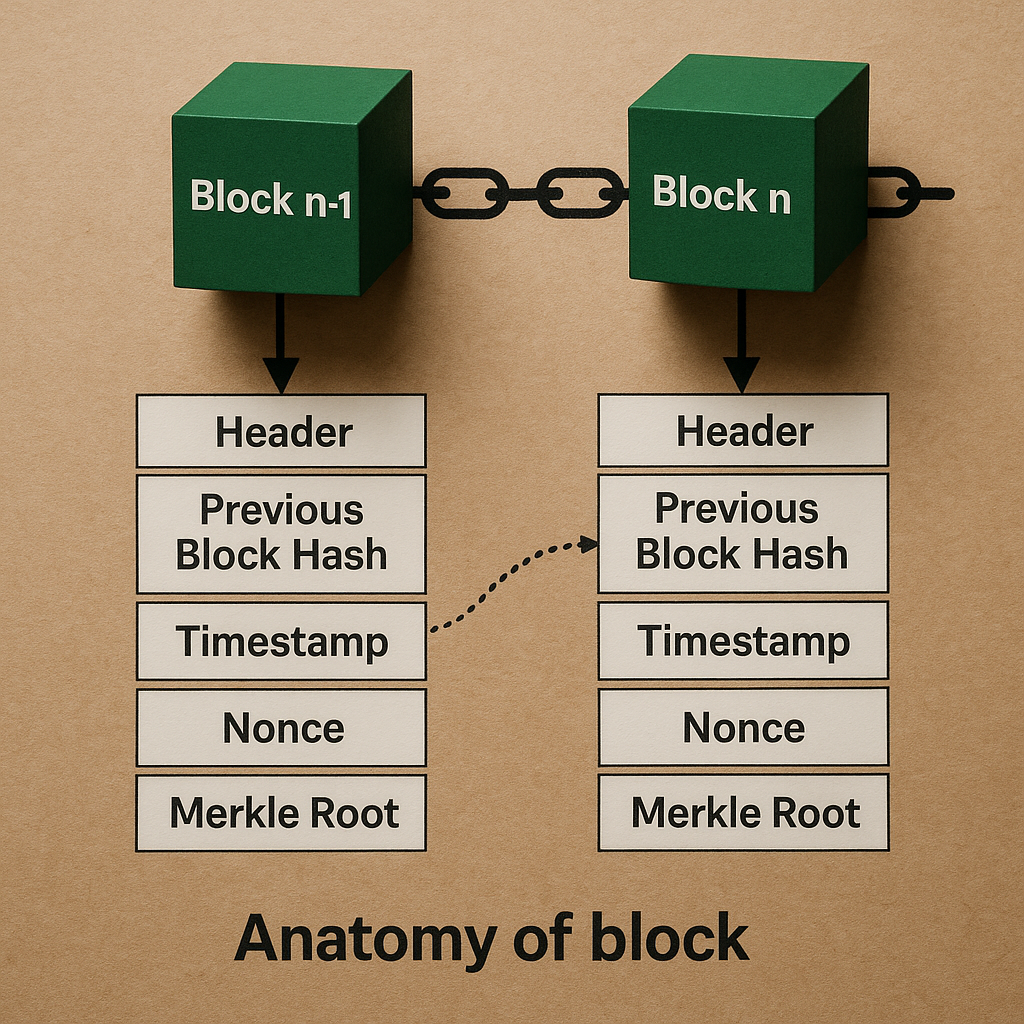
A compact data structure containing essential metadata including version numbers, difficulty targets, and cryptographic references that enable other nodes to quickly verify the block's legitimacy
A unique 256-bit identifier that cryptographically links this block to its predecessor, creating an unbreakable chain where altering any previous block would immediately be detected
A single hash that mathematically represents all transactions in the block, allowing quick verification that no transactions have been tampered with since the block was created.
Records the exact moment when the block was mined, enabling the network to maintain chronological order and enforce time-based rules.
A 32-bit "number used once" that miners continuously modify during the mining process to find a hash that meets the network's difficulty requirements.
The storage area containing the actual transaction data, digital signatures, and smart contract executions that users initiated.
Chain Formation
Chain formation is the process by which individual blocks become permanently linked together, creating an immutable historical record. This linkage mechanism is what gives blockchain its revolutionary security properties.
Blocks are cryptographically linked in chronological order: Each new block mathematically depends on all previous blocks through hash references, creating a timeline that cannot be altered without detection.
Each block references the hash of the previous block: This creates a dependency chain where changing any historical block would require recalculating every subsequent block's hash.
This creates an unbreakable chain of data: The mathematical impossibility of reverse-engineering hash functions means that once blocks are linked and confirmed, they become practically immutable.
The genesis block is the first block with no predecessor: This special foundational block is hardcoded into the blockchain protocol and serves as the starting point for the entire chain.
How New Blocks Are Added
The process of adding new blocks to a blockchain involves multiple validation steps and network consensus. This systematic approach ensures that only legitimate transactions are permanently recorded while maintaining the network's security and integrity.
Transaction Initiation
Transaction initiation is the starting point of the blockchain process, where users create and broadcast their intended transfers or smart contract interactions to the network. This phase establishes the foundation for all subsequent validation and security measures.
When someone wants to send cryptocurrency or execute a smart contract, they create a digitally signed transaction and transmit it to multiple network nodes simultaneously.
Each transaction contains complete information needed for validation, including cryptographic proof that the sender authorized the transfer.
Thousands of computers across the network independently check that transactions follow proper protocols and contain all required fields.
Approved transactions are temporarily stored in each node's memory until miners or validators select them for inclusion in the next block.
Block Creation Process
Block creation is where individual transactions are assembled into organized structures that can be added to the blockchain. This process involves careful selection and arrangement of transactions to maximize efficiency while adhering to network protocols.
Block creators choose which pending transactions to include, often prioritizing those with higher fees to maximize their rewards.
Transactions are arranged in a specific format with proper headers, merkle tree organization, and required metadata.
Most blockchains impose size restrictions (like Bitcoin's 1MB limit) to prevent blocks from becoming too large for the network to handle efficiently.
Block creators balance including high-fee transactions with technical constraints to optimize their economic returns.
Validation Requirements
Validation requirements form the security backbone of blockchain networks by establishing strict criteria that every transaction must meet before inclusion. These rules prevent fraud, double-spending, and other malicious activities that could compromise network integrity.
Each transaction must be cryptographically signed by the sender's private key, proving ownership and authorization without revealing the private key itself.
The network verifies that senders actually possess the cryptocurrency they're attempting to transfer, preventing overdrafts and fraudulent transactions.
Every transaction must follow specific data structures, field requirements, and protocol standards established by the blockchain's consensus rules.
The network maintains a record of all unspent transaction outputs (UTXOs) and rejects any transaction that tries to spend the same cryptocurrency twice.
Consensus Mechanisms: The Heart of Security
Consensus mechanisms are the democratic protocols that enable thousands of independent computers to agree on a single version of truth without central authority. These systems solve the fundamental challenge of distributed computing: how to ensure all participants reach the same conclusion about which transactions are valid and in what order they occurred.
Proof of Work (PoW)
Proof of Work is the original consensus mechanism that powers Bitcoin and established blockchain's credibility as a secure technology. It transforms the abstract concept of digital consensus into a tangible competition based on computational effort, making attacks economically prohibitive while ensuring network security.
Thousands of specialized computers (miners) race to solve cryptographic puzzles that require immense computational power, with the winner earning the right to add the next block and receive cryptocurrency rewards.
Mining requires dedicated hardware (ASICs) consuming significant electricity, creating a real-world cost that anchors digital security to physical resources and energy expenditure.
The miner who first discovers a valid solution broadcasts it to the network, and other miners immediately verify and accept the solution, starting work on the next block.
Other network participants can quickly verify the winning solution (taking milliseconds versus hours to find), ensuring the winner followed the rules without requiring the same computational effort.
Bitcoin pioneered this method in 2009, followed by Litecoin, Dogecoin, and Ethereum (before its 2022 transition), proving the mechanism's reliability across different cryptocurrencies.
Proof of Stake (PoS)
Proof of Stake represents a revolutionary evolution in consensus mechanisms, replacing energy-intensive mining with an elegant system based on economic stake and cryptographic randomness. This approach maintains security while dramatically reducing environmental impact and enabling faster transaction processing.

Validators are chosen to create new blocks based on the amount of cryptocurrency they "stake" (lock up as collateral), creating a system where those with the most to lose from network failure have the most influence over its operation.
Unlike mining's massive electricity consumption, PoS requires only standard computer hardware running lightweight software, reducing energy usage by over 99% compared to Proof of Work systems.
Validators must deposit significant amounts of cryptocurrency as stake, which can be "slashed" (permanently confiscated) if they attempt to validate fraudulent transactions or attack the network.
Advanced cryptographic algorithms randomly select validators from the pool of stakers, with higher stakes increasing selection probability while preventing any single entity from controlling block production.
Ethereum successfully transitioned to PoS in 2022, joining Cardano, Polkadot, and Solana in demonstrating that this mechanism can secure billions of dollars in value while maintaining decentralization.

Delegated Proof of Stake (DPoS)
Delegated Proof of Stake creates a representative democracy within blockchain networks, where token holders vote for trusted delegates to validate transactions on their behalf. This system balances decentralization with efficiency by reducing the number of active validators while maintaining democratic oversight.
Token holders vote for delegates who will represent their interests, similar to electing representatives in political systems, ensuring that validation power reflects community preferences.
A limited number of elected delegates (typically 21-101) handle transaction validation, enabling faster processing than systems where thousands of nodes must reach consensus.
Fewer validators mean quicker decision-making and higher transaction throughput, making DPoS suitable for applications requiring rapid confirmation times.
Delegates can be voted out for poor performance, creating ongoing incentives for honest behavior and responsive service to the community.
Proof of Authority (PoA)
Proof of Authority represents a consensus mechanism designed for enterprise and consortium blockchains where known, trusted entities validate transactions. This approach prioritizes efficiency and regulatory compliance over pure decentralization, making it ideal for business applications.
Network operators select validators based on identity verification and reputation, ensuring only trusted parties can participate in consensus decisions.
Commonly deployed in private blockchains for supply chain tracking, corporate record-keeping, and government applications where regulatory compliance is essential.
Eliminates competitive mining or staking, enabling near-instantaneous transaction confirmation with minimal computational overhead.
Security relies on the established reputation and legal accountability of validator organizations rather than cryptoeconomic incentives.

